Information Management & Computer Security(Series) · OverDrive: ebooks, audiobooks, and more for libraries and schools

Risk Management for Computer Security: Protecting Your Network and Information Assets: Jones, Andy, Ashenden, Debi: 9780750677950: Amazon.com: Books

Computer Information Systems (CIS) vs. MIS, Computer Science, IT, Cybersecurity, and Data Science - YouTube

M.S. in Business Analytics and Information Management + M.S. in Cybersecurity - Electrical & Computer Engineering
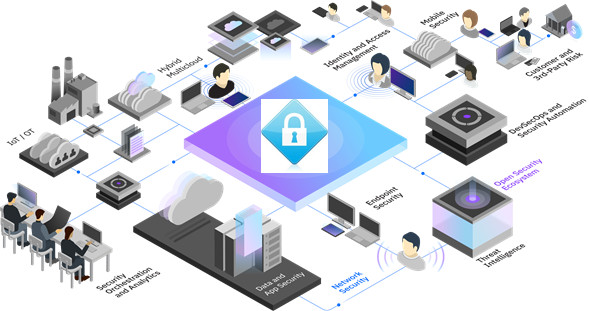
Information Security Management – View through the Digitization lens - ::iExperts Magazine:: Cyber Security - IOT - Big Data - IT Management Technical Articles and more ...