NetBIOS: what it is, how it works and how to use in information security - Ethical hacking and penetration testing

NetBIOS: what it is, how it works and how to use in information security - Ethical hacking and penetration testing
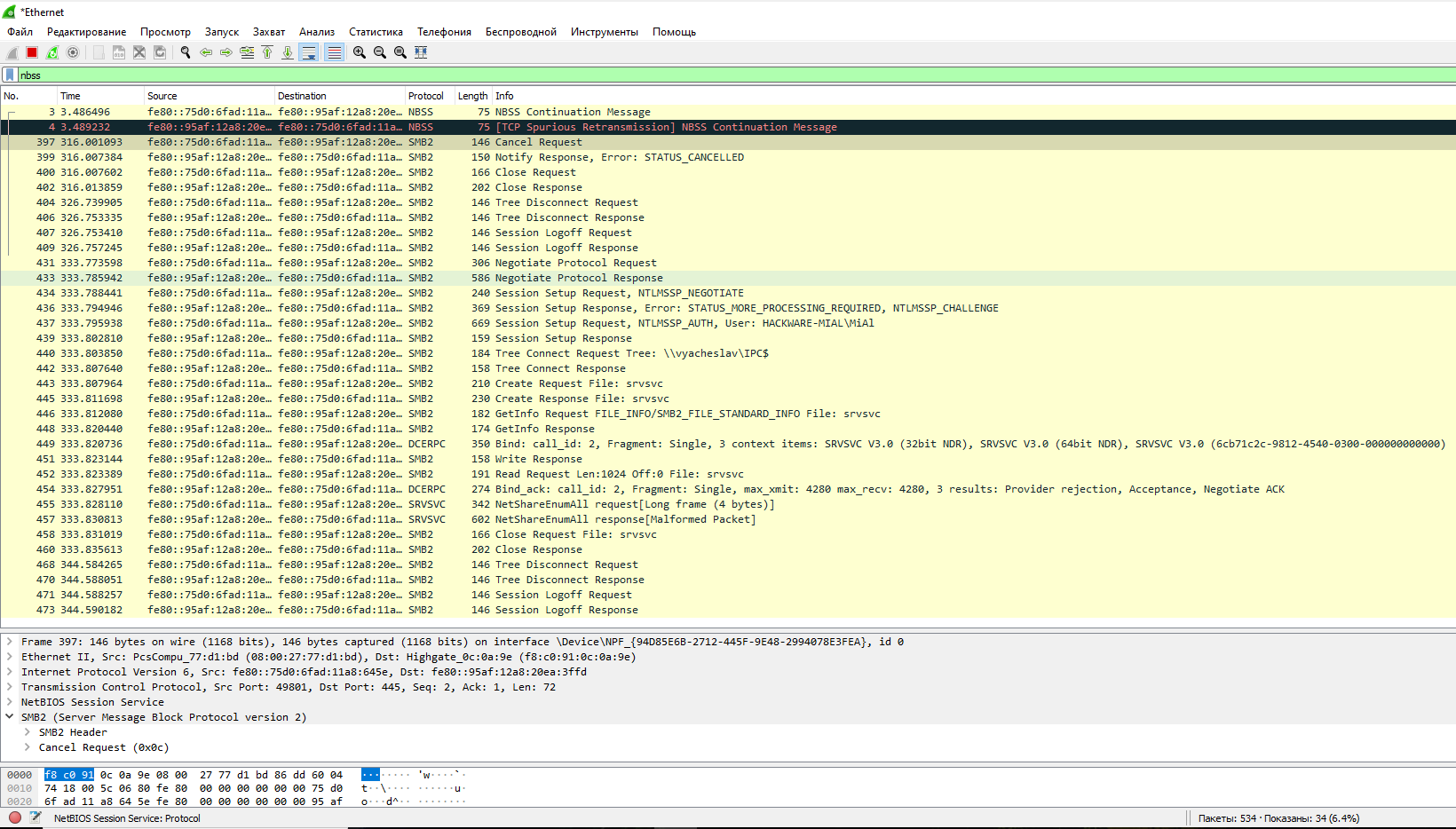
NetBIOS: what it is, how it works and how to use in information security - Ethical hacking and penetration testing

NetBIOS: what it is, how it works and how to use in information security - Ethical hacking and penetration testing

NetBIOS: what it is, how it works and how to use in information security - Ethical hacking and penetration testing
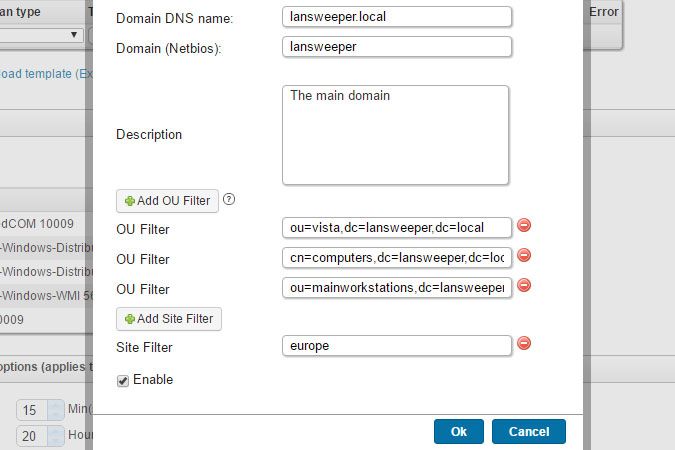
Scanning with an Active Directory Domain scanning target - Scanning your network - Lansweeper Community