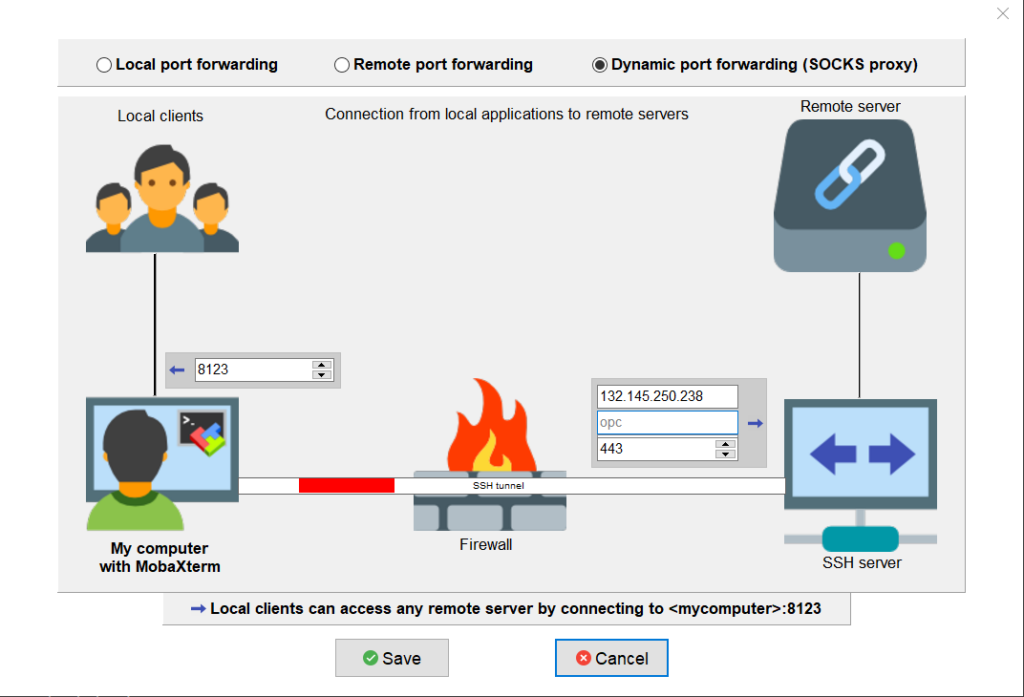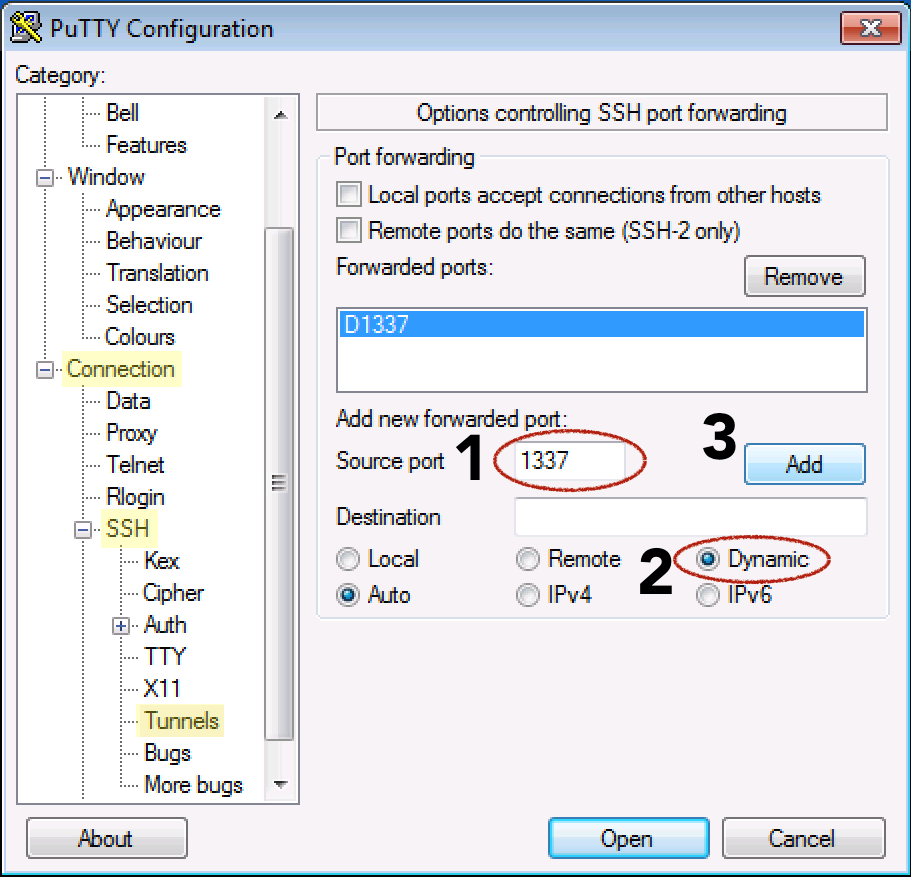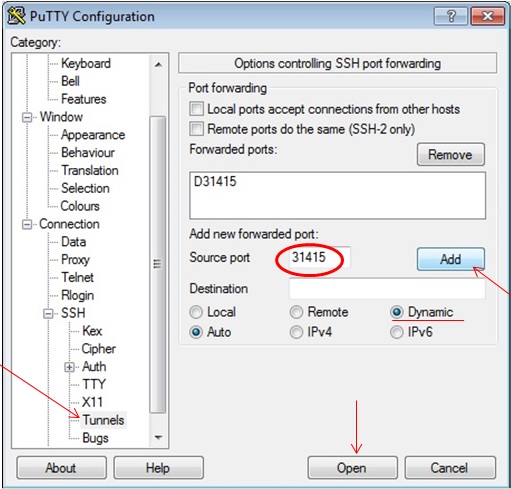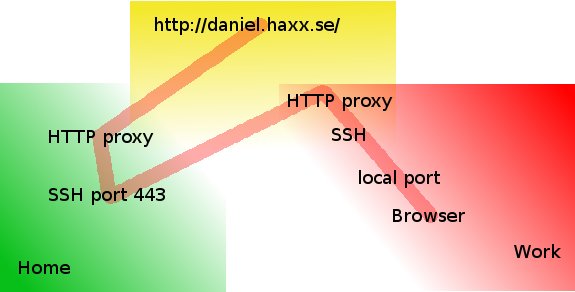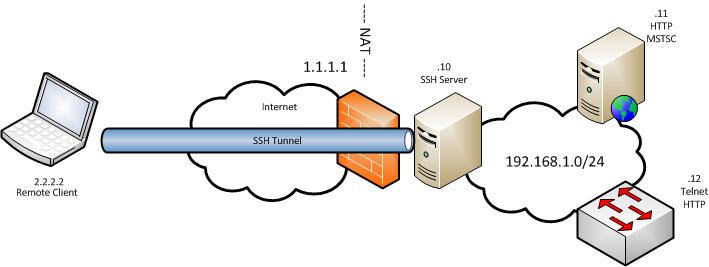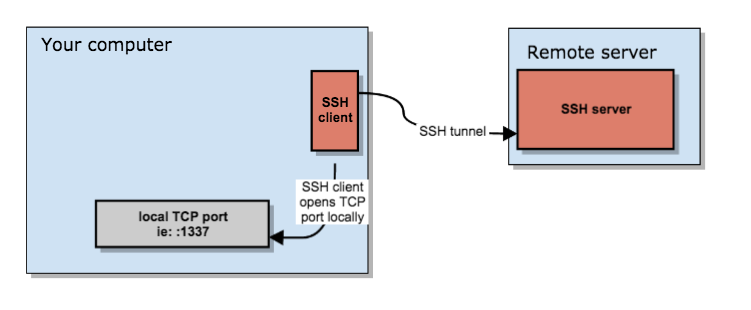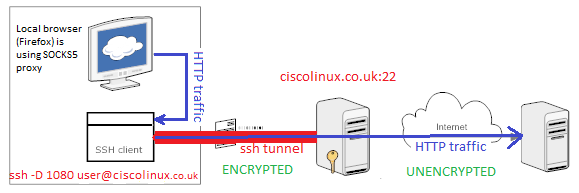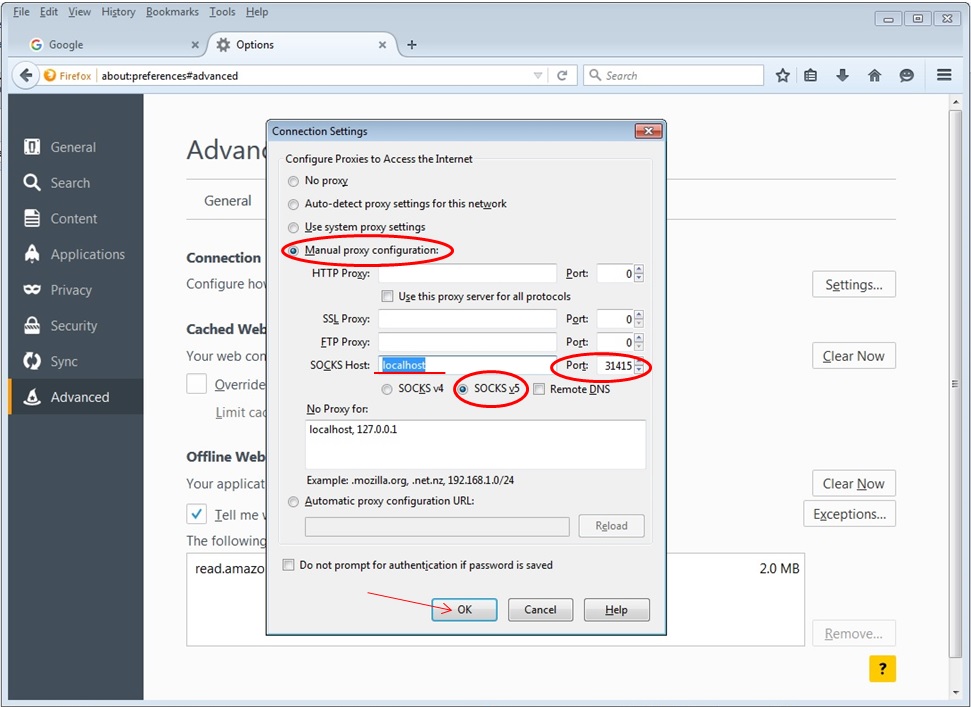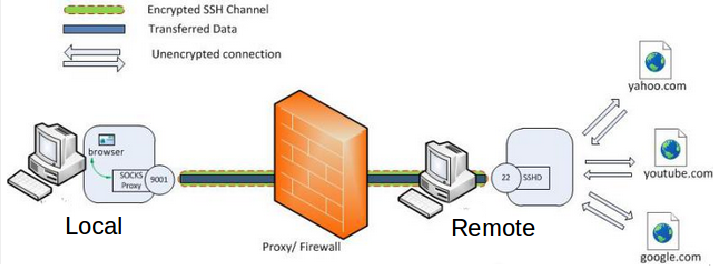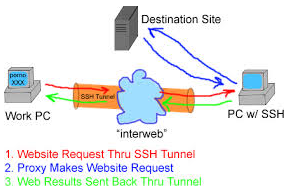
Secure your work PC internet traffic using SSH Dynamic Tunnel as Proxy to get around Corporate Spy Proxy and Site Filtering - ☩ Walking in Light with Christ - Faith, Computing, Diary
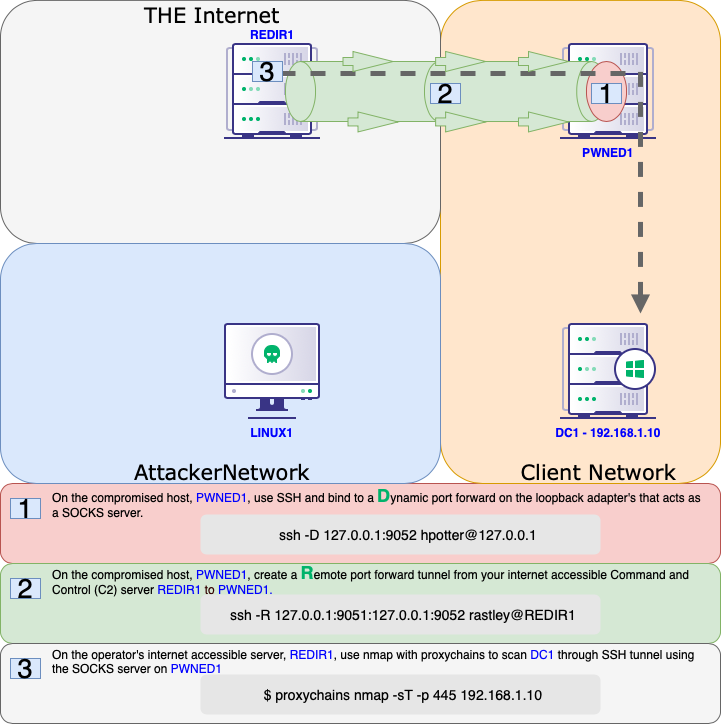
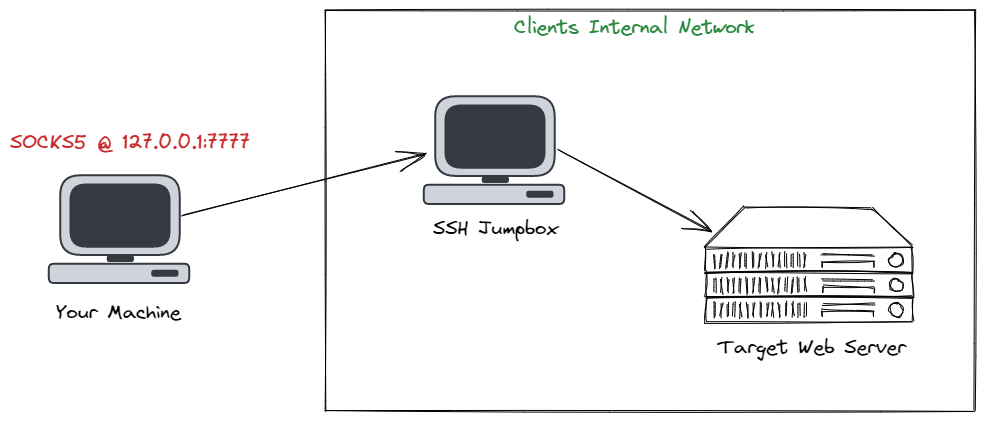
Offensive Security Guide to SSH Tunnels and Proxies - Malware News - Malware Analysis, News and Indicators
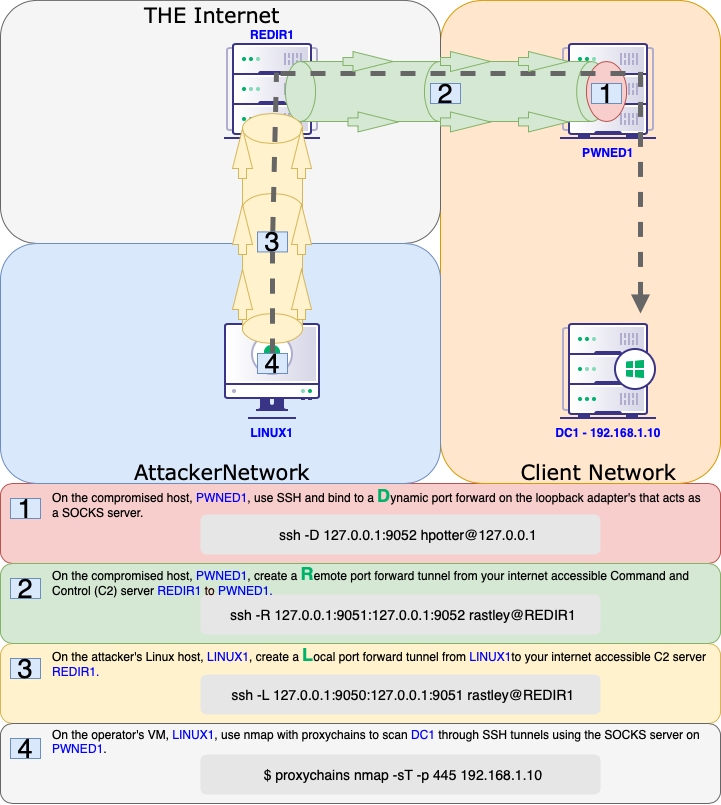
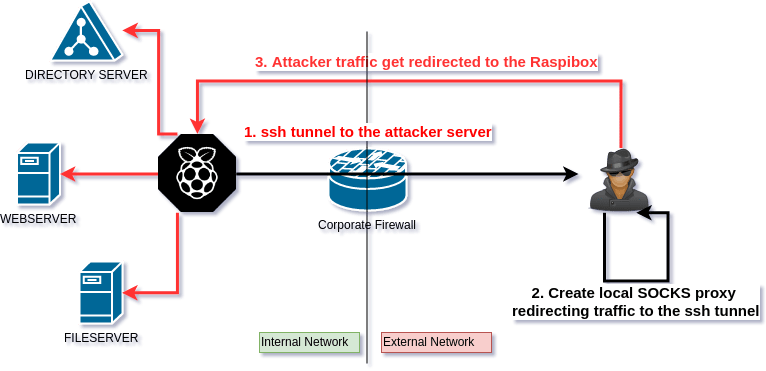
Offensive Security Guide to SSH Tunnels and Proxies | by Russel Van Tuyl | Posts By SpecterOps Team Members
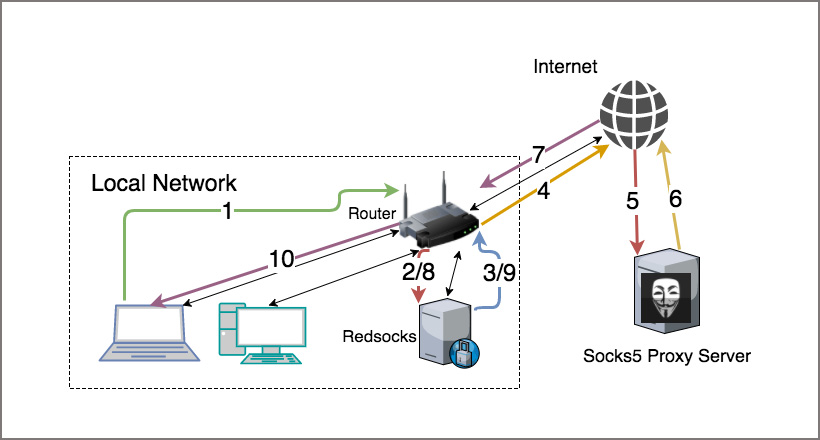
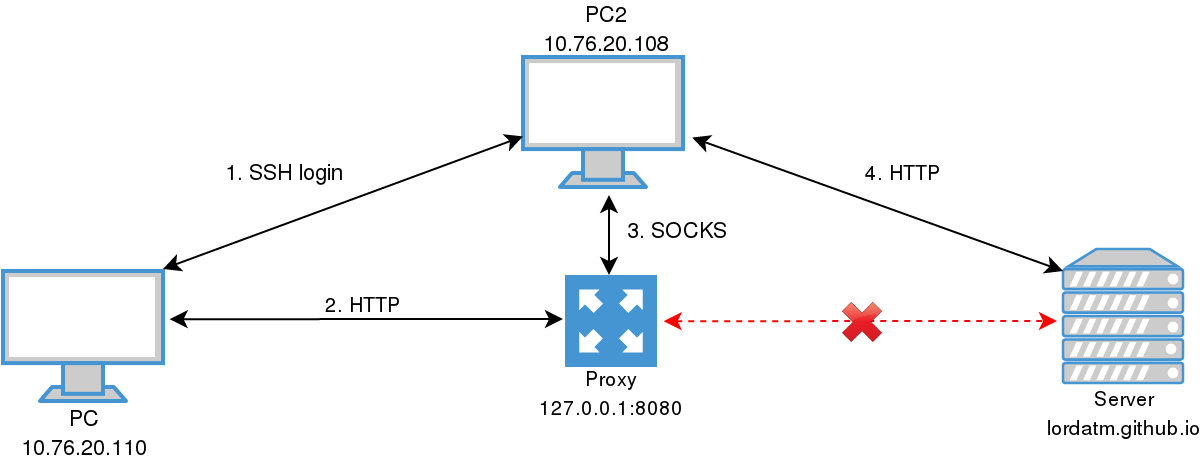
How to Route All Network Traffic from your LAN securely through a SOCKS5 proxy + SSH Tunnel + Redsocks | DNSFLEX